Reset Factory Laptop Would the Hacker Continue
Will a Factory Reset Remove Malware and Viruses?

Erasing all your data to get rid of some malware is never an easy choice. If you're going to do it, better know your success odds because, as I'm about to show you, not all viruses and malware go away during such a reset. So believe me, you need to be aware of the following information!
The factory reset removes malware and viruses, though not in 100% of cases. Nasty rootkits, for instance, don't go away with a reset. And sometimes, malware can resurface from an infected backup, recovery partition, or another device in the network.
The answer to whether a factory reset will remove malware and viruses depends on various factors, from infection vectors to infection targets. And then, there's also the issue of distinguishing between malware and viruses. But because a factory reset is p retty much like the nuclear option, b uckle up and let me show you what you need to know before pressing the red button.
Places where malware and viruses can hide from factory reset
This type of reset implies that you remove all stored data and bring your device to the same state it was in, back when it was released from the factory.
You didn't get your computer infected with malware or viruses when you took it out of the box. So, what's this? Why doesn't a return to the factory state guarantee you a virus-free device?
As mind-boggling as it looks, there's a simple – technical, but simple – explanation for it:
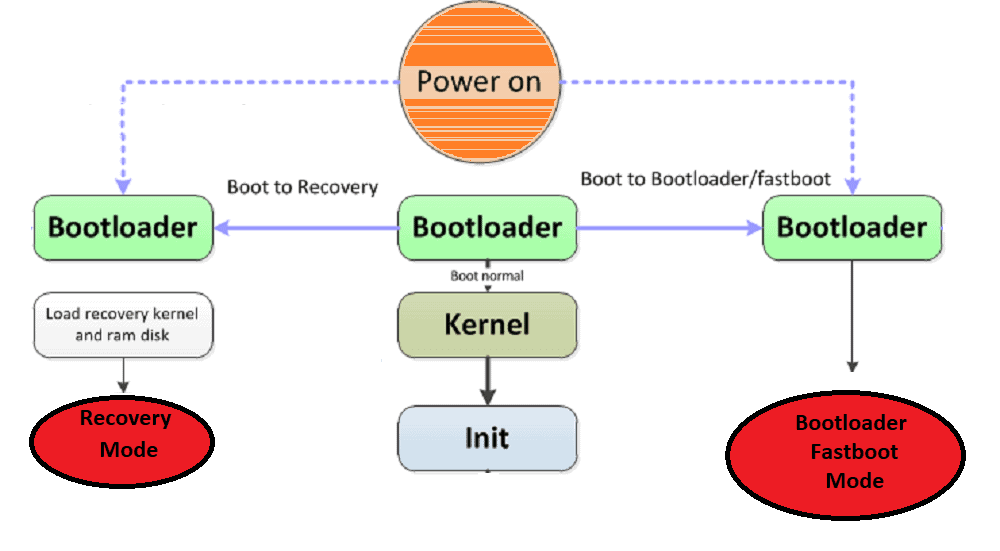
- Some viruses end up in a place where the factory reset has no power:
The firmware
The kernel
The startup code:
MBR (Master Boot Record)
VBR (Volume Boot Record)
The boot sector
2.Some viruses just sit in a nearby environment and get back to your PC on the first occasion:
The backup
The recovery partition
Other devices from the network:
A router
A printer
A camera
If the virus is somewhere where the factory reset has no access, its removal may require specialized equipment or even hardware replacement. That's right; some viruses can damage the hardware.
If the virus is in a backup or on another device from the network, the factory reset will remove it from your PC. But as soon as you access that backup or connect your computer to the infected network, it can get back on your PC. This makes it look as if it hadn't left your computer in the first place, which is not true.
The fact is that malware is getting more and more sophisticated. Difficult not only to find but also to remove. It only makes sense that there will be situations when the factory reset is the only option and instances when, unfortunately, the reset is not a practical option.
Next, I'd like to discuss malware and virus removal through a factory reset separately.
Can malware survive a factory reset?
Between malware and viruses, the former is the broader term. It encompasses any software with malicious intent. No matter how it works, what it does, or how it spreads, if it causes harm, it's malware.
Viruses left aside, other main categories of malware that can survive a factory reset would include trojans, worms, and rootkits. While these are not that common, their ability to escape a reset depends on where they reside.
When a hacker writes the code for some malware, an essential part of it implies indicating the malware's constituents' directories on the infected device. A reset will not overwrite the entire operating system. And depending on where the malware will reside, it can make it through the reset.
Some instances of nasty malware
If you run the reset from a recovery partition that the malware already infected, recovering your data from there might lead to the malware resurfacing.
Rootkits are notorious for their persistence, since the moment they get into the BIOS, they can theoretically survive pretty much anything you throw at it.
Worms have a higher chance to resurface once you reconnect your freshly reset device to the infected network since they are standalone programs that self-replicate within a network.
The list of examples could go on and on. The point is that malware defines a wide range of more or less sophisticated malicious software that may survive the factory reset depending on various factors.
Even so, there is consensus among cybersecurity experts that malware impossible to remove is rather difficult to bump into, at least for the average user. The type of malware you're getting from surfing the web, including porn websites, is more likely from those that will go away with a reset.

Does wiping a computer get rid of viruses?
Viruses are a specific type of malware. They attach to legitimate programs or files and are distributed through emails, flash drives, and, of course, infected files. They only activate following the victim's deliberate action of opening the compromised file or application.
Once a virus becomes active on your device, it can disable system functions, modify specific applications, and even encrypt or delete files.
File infectors are a common type of virus that spreads through executable files, usually within a network. If you reconnect to the same network that shares infected files, you can deal with the virus again shortly after the factory reset.
Polymorphic viruses, which are more complex, use self-replication and self-encryption mechanisms that allow them to change their code countless times and evade detection. Such shape-shifters can infect your system images, so if you opt to restore a previous image, there's a chance you won't get rid of it too quickly.
Most common instances when viruses survive factory reset
The instances when a factory reset will not remove viruses and malware are not that many. Consider the following:
Using an infected recovery partition for the reset
Recovery partitions are the built-in equivalent of restore disks.
The problem: because it resides on your PC, it is possible for a recovery partition to be infected.
The solution: to avoid all risks, don't use the recovery partition at all. Instead, install the operating system from a recovery CD or USB stick.
Know, however, that this situation, while possible, is far from common. There are currently no malware instances known to particularly target recovery partitions. Consequently, even if yours gets compromised, it would be a consequence of how the malware spreads and not a deliberate attack on the recovery partition.
This detail makes a huge difference. When the infection is tangential, the infected binaries will only run on the infected system. Following the system restore and reboot, those binaries should disappear, leaving you with no risk of dealing with the malware again.
For an infected recovery partition to give you severe problems, the hacker would have to orchestrate a precise attack. Developing malware that doesn't impact a wide range of devices is an unproductive activity that no hacker has a real interest in. That's why the odds of you dealing with a virus that goes after your recovery partition are so low.
Restoring an infected backup after the factory reset
This is a common mistake that doesn't have to do with the reset failing to remove the malware.
The problem: you may have a clean system to work with after the reset, but restoring an infected backup will make it look like the factory reset didn't do anything.
The solution: there are two workarounds for this issue. You can choose to give up on your backup altogether and accept losing all the data. OR you can keep your backup externally and only activate it once you have a clean OS and an antivirus installed so that you can scan its content.
As far as backup best practices are concerned, you could keep an external drive connected to your PC and regularly create backups on it, or you could use a cloud service.
The cloud is the safer option because service providers scan the data you store with them to keep their servers secure. So, technically, if your backup is infected, you have higher chances to be notified about it when you store it in the cloud than if you'd keep it on your external hard drive.
Dealing with a rootkit malware
A rootkit is a program that gives the attacker root-level access to your operating system. When corrupted by malware, it becomes complicated to detect, let alone to remove.
You could get it automatically, through a drive-by download, or manually installed by an attacker. The latter implies that the hacker obtained admin access to your device through a vulnerability exploit (like a privilege escalation) or phishing attach that leaked your password.
The problem: rootkits gain full control over your system, meaning they can also evade the software that was supposed to detect them. One particular version, also known as bootkit, will overwrite the MBR (Master Boot Record). Since you're using the MBR for performing the factory reset, you won't get rid of it not even after the reset. Other rootkits can get into the kernel or firmware, which, again, makes it almost impossible to remove.
The solution : signature scanning and difference scanning, behavioral and memory dump analysis are just a few of the more sophisticated attempts to identify and isolate a rootkit. For versions that affect the kernel or the firmware, removal may be impossible without specialized equipment or even some hardware replacement, as you can't use the APIs that Windows typically provides for such tasks. With bootkits removal, boot and nuke programs (such as DBAN) or disk-partitioning tools (see EaseUS) could be of help.
Connecting to a network with infected devices
With secondary device infections, your clean PC will likely get the malware once again the first time you connect to it. While somewhat new, such infections are on the rise because of the increased use of cloud services for either home or office networks.
The problem: routers and printers or webcams are some of the most common secondary devices that can host malware and easily infect your computer since they are all connected to the same network.
The solution: to avoid such issues, protect not just your PC, but every component connected to the network. Keeping software up to date, get the best security tools you can afford, and tweak security settings rather than letting them run by the defaults.
Examples of malware that wasn't removed by factory reset
Malware that doesn't go away with a factory reset is not that common, but it is guaranteed to make the headlines for quite some time when it does show up.
Take, for instance, the Android Trojan xHelper discovered in 2019. Users would get it after being redirected to websites hosting Android apps. Once they downloaded a compromised app from there, the trojan would install itself as a different, stand-alone service.
Uninstalling the original app did not affect the presence of xHelper, which continued to annoy with spam notifications and popups. For ten long months, Android users complained that xHelper was impossible to remove. Eventually, Malwarebytes for Android app came with an effective solution against it.

*
In 2018, ESET reported it had uncovered malware exploiting the UEFI. Lojax, the UEFI-based malware, was attributed to some Russian state-sponsored hackers. It was tough to get rid of Lojax because it would add UEFI rootkit to the firmware image, with the sole purpose of dropping the malware into the Windows OS partition, therefore automatically execute itself at startup.
*
Even more recently, in 2019, Kaspersky Lab reported another UEFI rootkit inflicting Windows 10 devices, this time attributed to Chinese hackers. The malware would automatically create a Trojan file on the infected machine, a file named "IntelUpdate.exe" and located in the Startup Folder. Even if identified and deleted by the user, it would reinstall itself.
*
As you can see, UEFI rootkits are particularly concerning. Many people would ask themselves – will a factory reset stop a hacker who resorts to UEFI rootkits? Most likely, no, not until the motherboard's firmware is updated to a clean, legitimate version. If this sounds like Chinese to you, then there's a high chance you won't be able to get rid of such malware in the event you get it yourself.
Understanding what a factory reset implies
A factory reset is nothing but a complete software restore of your computer. The process erases all the information stored on it, bringing the device to its original system state. All the settings, applications, and data will be wiped out, leaving you with an empty hard drive and all the original system settings your computer had when it was released from the factory.
Technically, the factory reset is a two-step process that implies:
1.Removing everything stored on it;
2.Restoring the operating system image.
A few things to consider before initiating the process
The factory reset is irreversible
Once you initiate it, there is no coming back. What's more, if you try to interrupt it, you'll end up with an unfunctional PC, in an unstable state, missing essential pieces of the puzzle that allows it to function correctly – as it could be without the operating system or specific applications or device drivers.
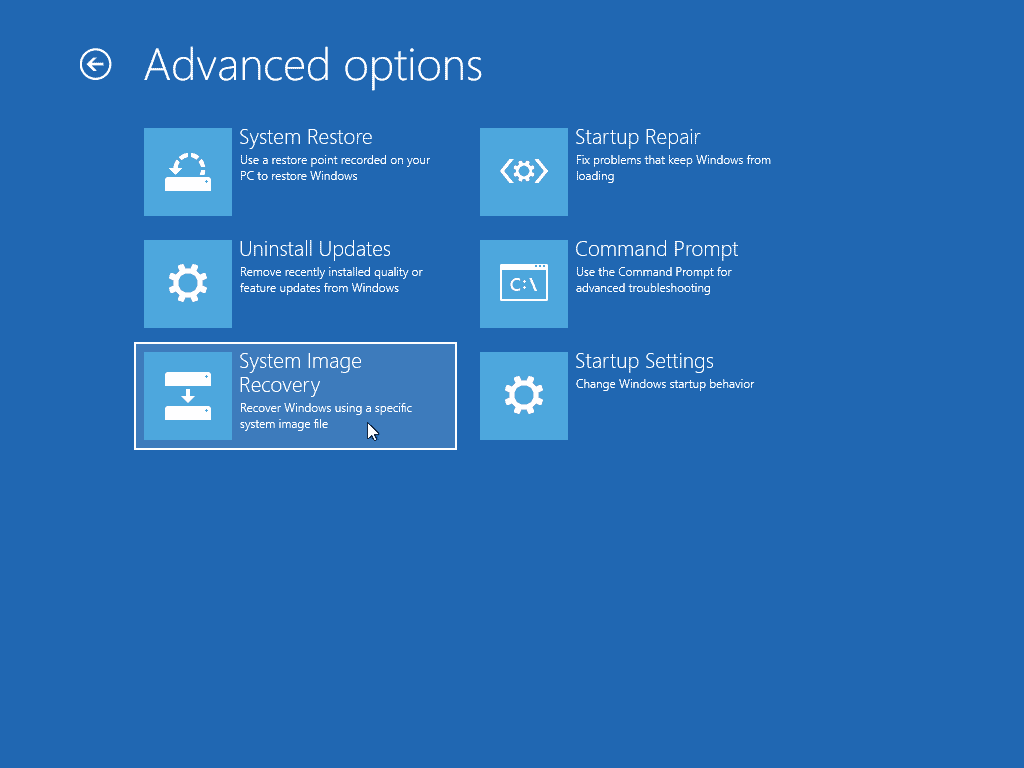
There's more than one system restore option
As discussed above, there is a small chance that the recovery partition is compromised. To be 100% sure that you're getting a clean OS version, you should use a recovery drive instead of the recovery partition. With a recovery CD, you will be guided through each step of the process, from formatting the hard drive to installing the OS and setting it up.
How to do a factory reset
As you can imagine, the steps for initiating such a reset vary from one device and one operating system to another. Below, I'll try to be brief but still list the main steps to follow at a glance:
How to factory reset your Mac
- Access the macOS recovery:
If your Mac has an Intel processor:
– Initiate a simple restart process from its menus;
– Right after that, hold down the Command and R keys simultaneously until you see the Apple logo on the screen;
– At that stage, you can release the keys and wait for the Mac to boot into Recovery mode.
If your Mac has an Apple silicon processor:
– First, shut down your Mac;
– Then, turn it back on, but don't release the power button – hold the button for a few seconds until the "Loading startup options" shows up on the screen;
– From there, go to Options;
– Finally, select macOS Recovery.
2.Select a user that has administrator privileges and use the account credentials to get access to the startup options;
3.Select the Disk Utility menu to begin the hard drive wiping;

4.Access the Internal heading, select the Macintosh HD drive, and hit the Erase button at the top toolbar;
5.In the dialog box that will show next, type the drive name (same as initially, Macintosh HD), and pick your desired format – either APFS or Mac OS Extended;
6.Finally, hit the Erase (or the Erase Volume Group) and watch it wiping the drive;
7.Repeat these steps to erase all the other internal drives if you have more than one;
8.Go back to the Recovery screen by leaving the Disk Utility window;
9.Proceed to reinstall your OS following the formatting steps from above, by connecting your Mac to a power source and activating the internet connection;
10.From within the same macOS Utilities screen, select the Reinstall macOS option;
11.Follow the prompts to download a new version of the OS and have it installed.
How to factory reset a Windows PC running on Windows 10
1.Hit the Start button and open up the Settings window from there;
2.Select the Update & Security icon;
3.A new window will open with a menu on the left side, from where you get to select the Recovery option;
4.At the right side of the same window, you'll see your Recovery options:
5.Select the Reset this PC option by hitting the Get started button underneath it;
6.If you're not logged in from an admin account, you'll next be prompted to enter an admin user name and password so you can proceed with the changes to the device;
7.A new Reset this PC window will launch afterward, with two options:
- Keep my files – this will remove apps and settings while keeping your personal files;
- Remove everything – this will remove personal files, apps, and settings.
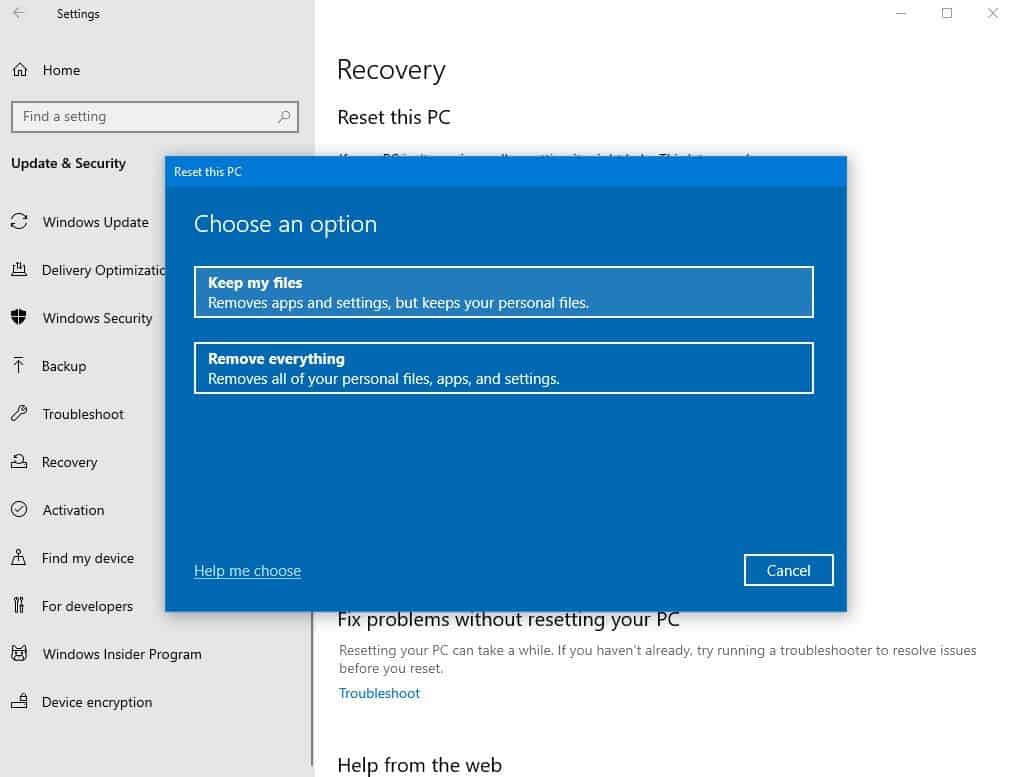
8.Select Remove everything and hit the Next button when the warning message shows up – it's just a reminder that it's an irreversible process;
9.Finally, hit the Reset button;
10.Click Continue in the next window.
What to do to avoid having to initiate a factory reset
By now, it should be clear that initiating a factory reset can be quite stressful. On the one hand, you can't be 100% sure that it will get you rid of the nasty malware or virus. On the other hand, you risk losing some critical files in the process or live with the frustration of not accessing your old backups.
Clearly, it's best to prevent rather than to fix. While the type of malware that is almost impossible to remove is not that common, you'll always be better taking as many precautionary measures as possible.
There are plenty of details you need to take into account. Assuming you're only willing to do one thing, let that be the selection of the best antivirus software you can get! If your main activity online involves browsing the web, you might want to check this guide on which antivirus programs offer you the best browsing protection.
Other than that, it can never hurt to adopt a series of best practices that will help you avoid unnecessary risks. Viruses may come from external drives, but most of them will come over the web. Once you know you have the best protection for the way you use your PC, make sure it's always up to date and keep an eye on the signs that it's time for a scan .
The way you use the internet is, after all, the decisive factor in the kind of experiences you're going to have. As you mind your own business, always stay vigilant and watch out for scam websites .
Remember, you can easily get viruses by visiting a website , so don't ignore your antivirus' messages. If it detects anything, whenever you're in doubt, ponder your options and choose the best action between quarantine, delete, or clean a virus .
Here is a complete guide on what to do when you are hacked. And here's a selection of valuable tips on how to protect your home Wi-Fi .
Never stop learning about the best practices for online security. Else, you're going to learn how terrible it feels to be hacked and how frustrating it is to get stuck with malware that not even a factory reset will remove!
Source: https://antivirusjar.com/will-a-factory-reset-remove-malware-and-viruses/
0 Response to "Reset Factory Laptop Would the Hacker Continue"
Post a Comment